MSI, a leading gaming PC hardware manufacturer, is grappling with the aftermath of a significant ransomware attack by a group called Money Message. The attackers claimed to have stolen critical data, including MSI’s source code, and are demanding a $4 million ransom to prevent the leak. With consumer trust and the company’s reputation on the line, this high-profile attack highlights the risks posed to businesses and consumers in today’s increasingly interconnected world.
A New Threat Emerges
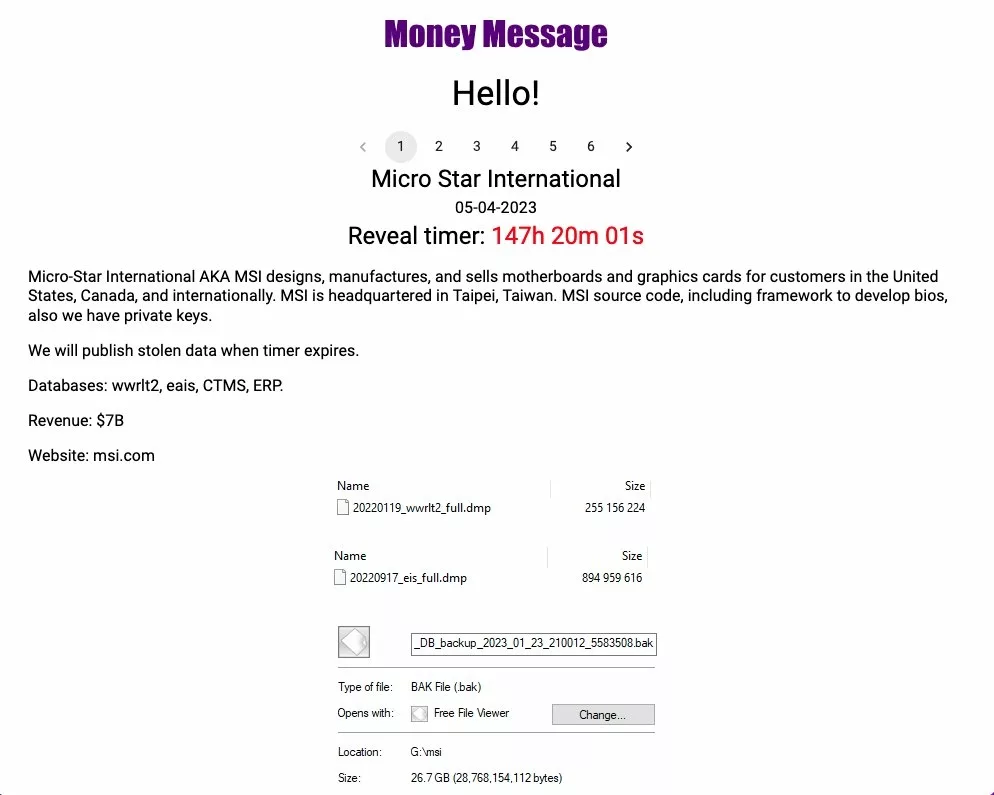
Money Message, a new ransomware group, is making headlines with bold attacks on global companies. In addition to MSI, the group has targeted other US, UK, and Bangladesh firms. The cybercriminals have set a countdown timer for over 100 hours on their website, warning that they will release the stolen data once the time is up.
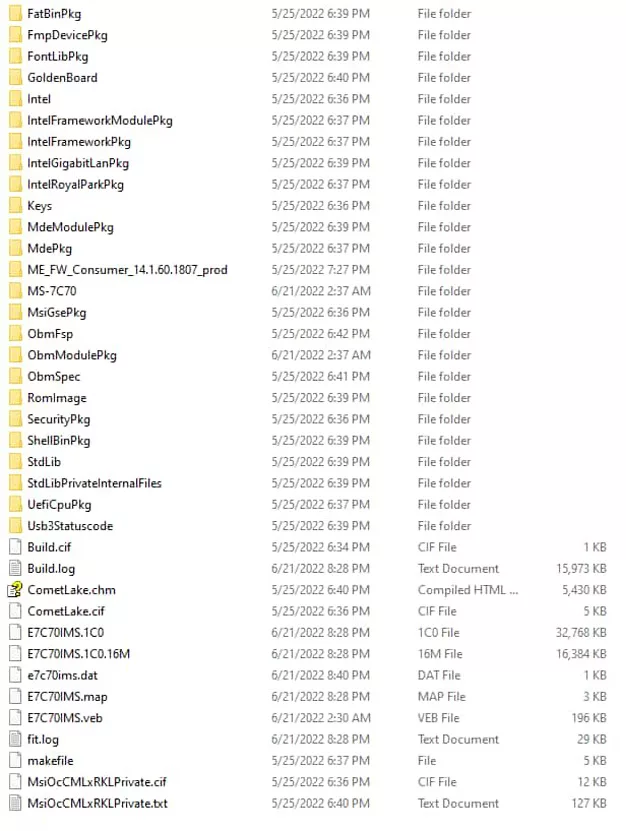
The data breach at MSI has exposed sensitive information, such as BIOS source code, CTMS and ERP databases, private keys, and BIOS firmware. While the company has acknowledged the attack and confirmed that its network was breached, the full extent of the damage remains unclear.
The Impact on Consumers
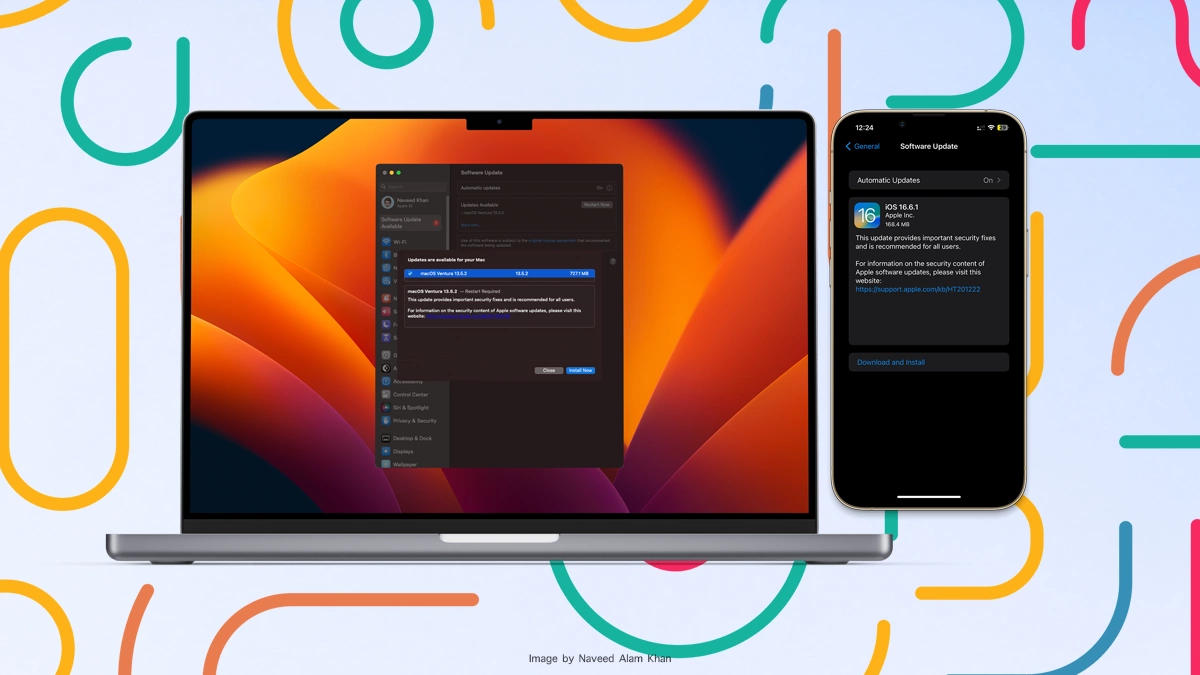
MSI’s customers are understandably concerned about the potential ramifications of this ransomware attack. The stolen source code could be used to create malicious firmware clones, tricking users into installing harmful software. To address this issue, MSI has urged users to download the latest firmware, and BIOS updates only from its official website. Avoiding files from third-party sources or driver update software will be best.
Additionally, the company has not disclosed whether customer data was compromised in the breach. If personal information has been exposed, MSI users could be at risk of identity theft, fraud, and other cybercrimes.
In a statement, MSI said:
After detecting some information systems being attacked by hackers, MSI’s IT department has initiated information security defense mechanisms and recovery procedures.
The company also reported the incident to authorities and added,
MSI urges users to obtain firmware/BIOS updates only from its official website and not to use files from sources other than the official website.
MSI Statement at Press Release
MSI’s Response and Future Outlook
In the wake of the attack, MSI has taken steps to mitigate the damage and restore normal operations. The company is working closely with law enforcement agencies and cybersecurity experts to address the situation.
However, the incident has raised questions about MSI’s cybersecurity measures and the potential long-term consequences for the company. In an industry where trust and brand reputation are vital, MSI must work diligently to reassure its customers and stakeholders that it is taking the necessary steps to prevent future attacks.
To that end, MSI has pledged to strengthen its cybersecurity architecture and management to ensure business continuity and network security. While the company’s response has been swift and proactive, the true test will come in the weeks and months ahead as it seeks to rebuild consumer trust and restore its tarnished reputation.
Proactive Steps and the Road Ahead
The MSI ransomware attack is a stark reminder of the ever-present threat cyber criminals pose. As technology becomes more ingrained in our daily lives, businesses and consumers must remain vigilant in safeguarding their digital assets and personal information.
MSI’s situation underscores the need for robust cybersecurity measures and the importance of educating users about the potential risks of downloading software from unofficial sources. The situation also highlights the need for greater collaboration between companies and law enforcement agencies in the fight against cybercrime.
In response to this attack, businesses and individuals should consider adopting more robust security protocols, such as multi-factor authentication, regular security audits, and employee training in cybersecurity best practices. By taking proactive steps, we can protect ourselves from future threats and ensure the integrity of our digital world.
The company must remain transparent and accountable as MSI navigates this challenging period. By sharing information about the attack and the steps to address it, MSI can demonstrate its commitment to protecting customer data and regaining the trust of its user base.
Looking forward, the tech industry must learn from this incident and prioritize cybersecurity to protect consumers and businesses. By investing in cutting-edge security measures and fostering a culture of awareness and preparedness, we can create a safer digital landscape for all.
The Ongoing Battle Against Cybercrime
The MSI ransomware attack is yet another reminder that cybercriminals are relentless in their pursuit of valuable data. As the threat continues to evolve, so too must our defenses. The collaboration between businesses, consumers, and law enforcement agencies is crucial in the ongoing battle against cybercrime.
In the meantime, MSI users and the wider tech community will watch closely as the situation unfolds. The company’s response to this crisis will undoubtedly serve as a case study for how businesses can recover from cyberattacks. With a proactive and transparent approach, MSI has the opportunity to turn this challenging situation into a valuable learning experience. Not just for itself but for the entire industry.
Source: BleepingComputer.com and MSI Press Release.





As a participant in the Amazon Associates Program and other affiliate partnerships, we are provided with affiliate marketing opportunities to help support our content creation efforts, read our Disclosure statement.